
We have recently provided technology support in organizing Data Hackathon for Robi Axiata (one of the top telecom companies in Bangladesh). It was for 2 days with 25 teams having 105 team members.
During facilitating this hackathon, we had to make sure the followings:
- Each team has a common URL to login AWS
- Each team can only access AWS SageMaker service
- They would be able to use only the following instance:
“ml.t3.small”,
“ml.t3.medium”,
“ml.t3.large”,
“ml.c5.large”,
“ml.m5.large”,
“ml.r5.large”,
“ml.r5.xlarge”4. Each team will have $150 of budget for the Hackathon
1. Each team has a common URL to login AWS:
We have done the following to serve the the above points:
We have used Single Sign-On service where AWS SSO was the identity provider and we have created all the users which were assigned to different groups for different accounts.
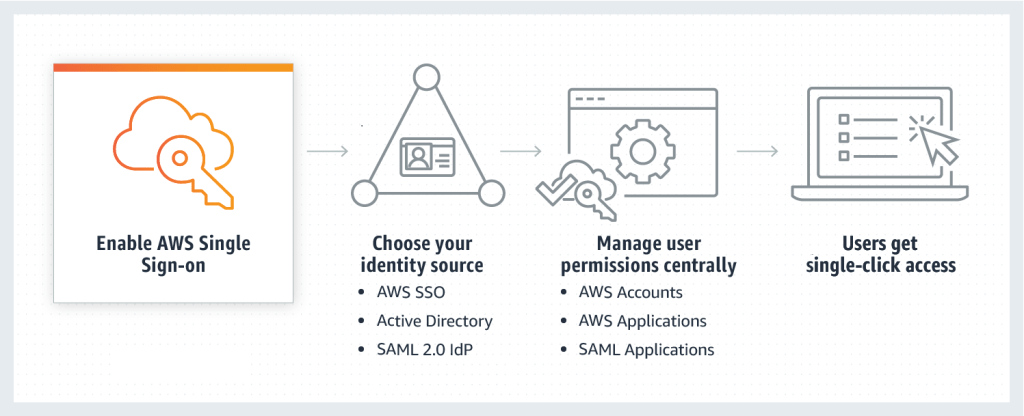
2. Each team can only access AWS SageMaker and relevant services
Following code was added in the policy for AWS SSO permission set to access the SageMaker which is given below:
{
“Version”: “2012-10-17”,
“Statement”: [
{
“Sid”: “SageMakerApis”,
“Effect”: “Allow”,
“Action”: [
“sagemaker:” ], “Resource”: ““
},
{
“Sid”: “VpcConfigurationForCreateForms”,
“Effect”: “Allow”,
“Action”: [
“ec2:DescribeVpcs”,
“ec2:DescribeSubnets”,
“ec2:DescribeSecurityGroups”
],
“Resource”: “” }, { “Sid”: “KmsKeysForCreateForms”, “Effect”: “Allow”, “Action”: [ “kms:DescribeKey”, “kms:ListAliases” ], “Resource”: ““
},
{
“Effect”: “Allow”,
“Action”: [
“codecommit:BatchGetRepositories”,
“codecommit:CreateRepository”,
“codecommit:GetRepository”,
“codecommit:ListRepositories”,
“codecommit:ListBranches”,
“secretsmanager:CreateSecret”,
“secretsmanager:DescribeSecret”,
“secretsmanager:ListSecrets”
],
“Resource”: “” }, { “Sid”: “ListAndCreateExecutionRoles”, “Effect”: “Allow”, “Action”: [ “iam:ListRoles”, “iam:CreateRole”, “iam:CreatePolicy”, “iam:AttachRolePolicy” ], “Resource”: ““
},
{
“Sid”: “DescribeECRMetaData”,
“Effect”: “Allow”,
“Action”: [
“ecr:Describe” ], “Resource”: ““
},
{
“Sid”: “PassRoleForExecutionRoles”,
“Effect”: “Allow”,
“Action”: [
“iam:PassRole”
],
“Resource”: “*”,
“Condition”: {
“StringEquals”: {
“iam:PassedToService”: “sagemaker.amazonaws.com”
}
}
}
]
}
3. Restricted instance size:
To ensure restricted instance size, following policy was added:
{
“Action”: [
“” ], “Resource”: [ ““
],
“Effect”: “Deny”,
“Sid”: “BlockSagemaker”,
“Condition”: {
“ForAnyValue:StringNotLike”: {
“sagemaker:InstanceTypes”: [
“ml.t3.small”,
“ml.t3.medium”,
“ml.t3.large”,
“ml.t3.xlarge”,
“ml.c5.large”,
“ml.m5.large”,
“ml.r5.large”,
“ml.r5.xlarge”
]
}
}
}
4. Each team will have $150 of budget for the Hackathon
To ensure that AWS budget alert has been added along with different milestone with AWS SNS (both SMS and email) to make sure we are acknowledged as soon any teams’ usage reached the threshold to do different action related to it.